Protect. Manage.
Enforce. Scale.
Transforming your IT, OT, IoT & IIoT solutions to be Resilient, Reliable, Scalable, and Secure


About Us
Manage every device. Secure every endpoint. All via one console.
Comprehensive Solutions for Modern Enterprises
Why Choose Us
30+ years of expertise in IT and IoT, delivering secure, end-to-end solutions across diverse domains—from infrastructure to automation and analytics. Experienced in telecom, manufacturing, food and agri-tech, ed-tech, BPO/KPO and software sectors.
Stay audit ready at all times with automated policy enforcement and real-time tracking. We help you align with frameworks like NIST, HIPAA, and ISO—without the manual overhead.
At MeKosha, Zero Trust is our foundation. Every user, device, and action are continuously verified to ensure uncompromised security across your IT, IoT, and IIoT environments
With native DLP, encryption, and IAM, we ensure proactive protection and policy-driven control across every endpoint enabling you to stay secure, compliant, and always in control.
A central control plane for complete visibility, action, and automation across your entire device ecosystem. We provide a single interface to manage devices across Windows, MacOS, iOS, ChromeOS, Android and Linux.
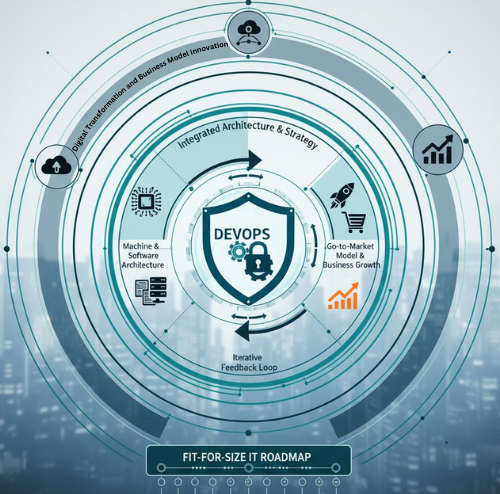
Our Approach
Our Proven 8-Step Framework for Scalable Endpoint Management
Assess & Discover
Auto-discover all devices (IT, OT, IoT, IIoT), classify by type, ownership, and risk posture.
Complete visibility across endpoints and shadow IT elimination.
Plan & Architect
Define policies, compliance needs, app deployment strategies, and user roles.
Customized MDM/UEM architecture aligned to org workflows.
Provision & Enroll
Onboard devices via zero-touch or QR enrollment, assign policies and profiles automatically.
Fast, standardized provisioning across user/device types.
Secure & Configure
Enforce security baselines: DLP, encryption, VPN, firewall, kiosk/ single/ multi-app modes.
Devices are policy-compliant, secure, and hardened from day one.
Deploy & Control
Push apps, updates, and content over-the-air; remote lock/ wipe; manage assets centrally.
Centralized control with minimal user intervention.
Monitor & Support
Real-time tracking of health, usage, compliance, and security posture. Provide remote support.
Proactive management, incident resolution, and policy updates.
Optimize & Report
Run lifecycle analytics, license audits, usage optimization, and compliance reporting.
Continuous improvement + audit readiness.
Retire & Recycle
Offboard devices securely, wipe data, update inventory, and prepare for reuse/replacement.
Secure deprovisioning and lifecycle closure.
Testimonials
What Our Clients are Saying
“
I have had the privilege of working with MeKosha Solutions, led by the exceptional Smideep and Ramnath, for a long time. Their team consistently demonstrates creativity, professionalism, and a deep commitment to excellence. MeKosha's expertise in IT infrastructure, security solutions, and compliance is unparalleled. They approach every project with integrity, ensuring innovative and reliable solutions tailored to client needs. Above all, their trustworthiness and dedication set them apart as partners. Whether it's managing complex deployments or delivering bespoke IT solutions, MeKosha Solutions is a name I wholeheartedly recommend for any organization looking for resilient and secure IT services.
”
Panos Leledakis
IFA Academy

“
Mekosha has made a promising start to our VAPT engagement, demonstrating a thorough understanding of our security requirements. Their initial approach and communication have been professional and reassuring. We look forward to seeing the value they bring to our security posture.
”
Jacob
Shivani Scientific

“
Mekosha Solutions has been an invaluable partner in strengthening our IT infrastructure. Their expert guidance and cost-effective solutions have significantly improved our operational efficiency and IT security.
”
SakshamGram

Get Started with OpenIY
Free Trial


News & Articles
Our Latest Blog Posts
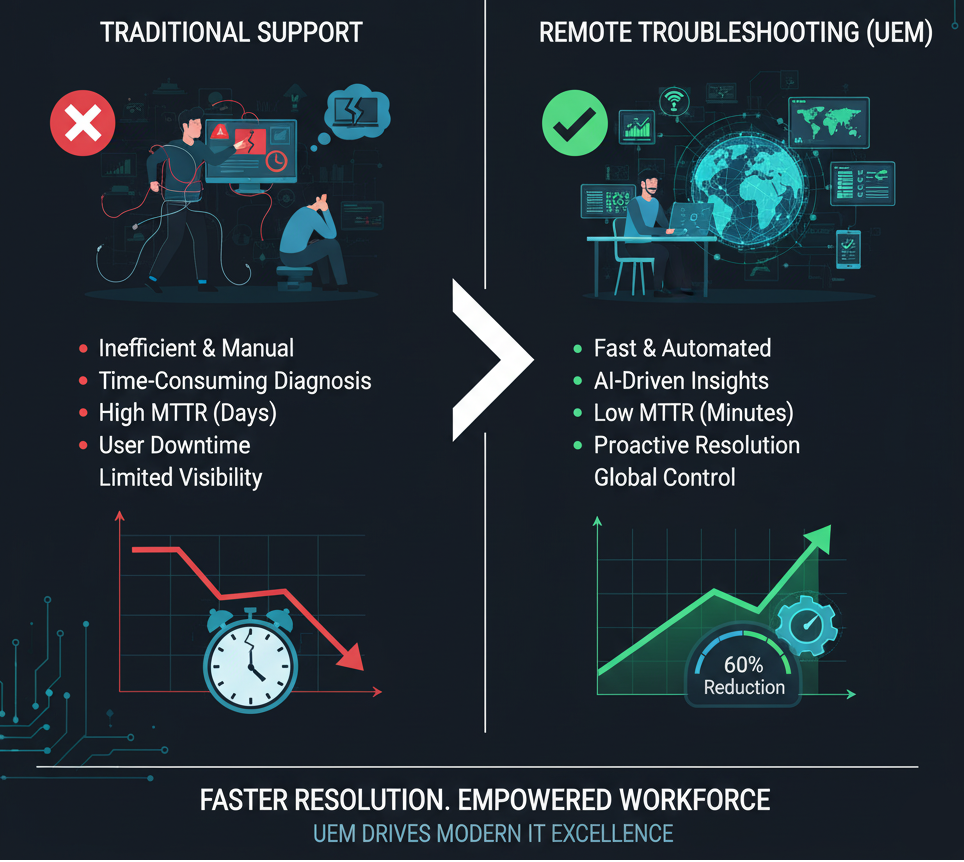
Remote Troubleshooting for the Win: Cut Down MTTR with UEM Insights
Remote Troubleshooting for the Win: Cut Down MTTR with…
Shadow Apps vs. Sanctioned Apps: What Your Endpoint Data Is Telling You
What Are Shadow Apps and Why Do They Matter?…

Predictive Maintenance with Asset Intelligence: Stay One Step Ahead of Device Failures
Predictive Maintenance with Asset Intelligence: Stay One Step Ahead…




