News & Articles
Our Latest Blog Posts
Oct 16, 2025
-
0 Comments
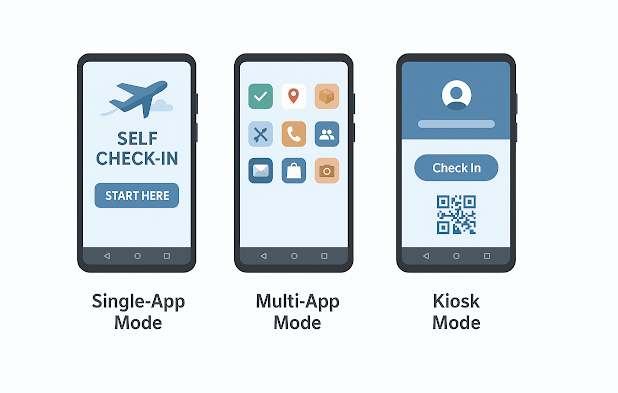
Why locking down your devices to Single-App, Multi-App, and Kiosk Mode is a game changer
Why locking down your devices to Single-App, Multi-App, and…
Oct 16, 2025
-
0 Comments
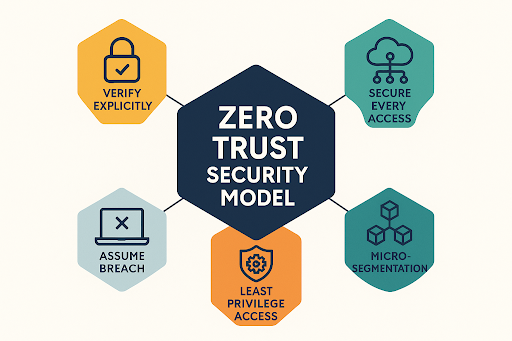
What Is Zero Trust and how does it impact endpoint security?
What Is Zero Trust and how does it impact…
Oct 16, 2025
-
0 Comments
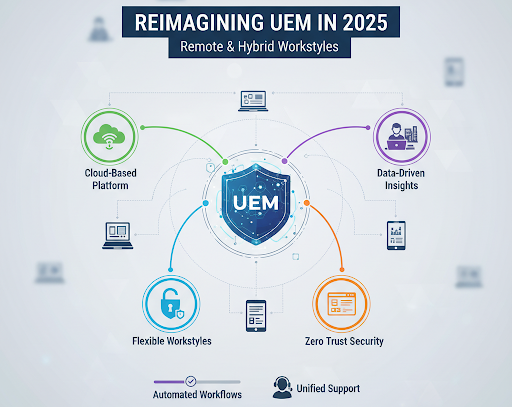
Support for Remote, Hybrid & Frontline Workers: Redefining Endpoint Management in 2025
Support for Remote, Hybrid & Frontline Workers: Redefining Endpoint…
Oct 16, 2025
-
0 Comments
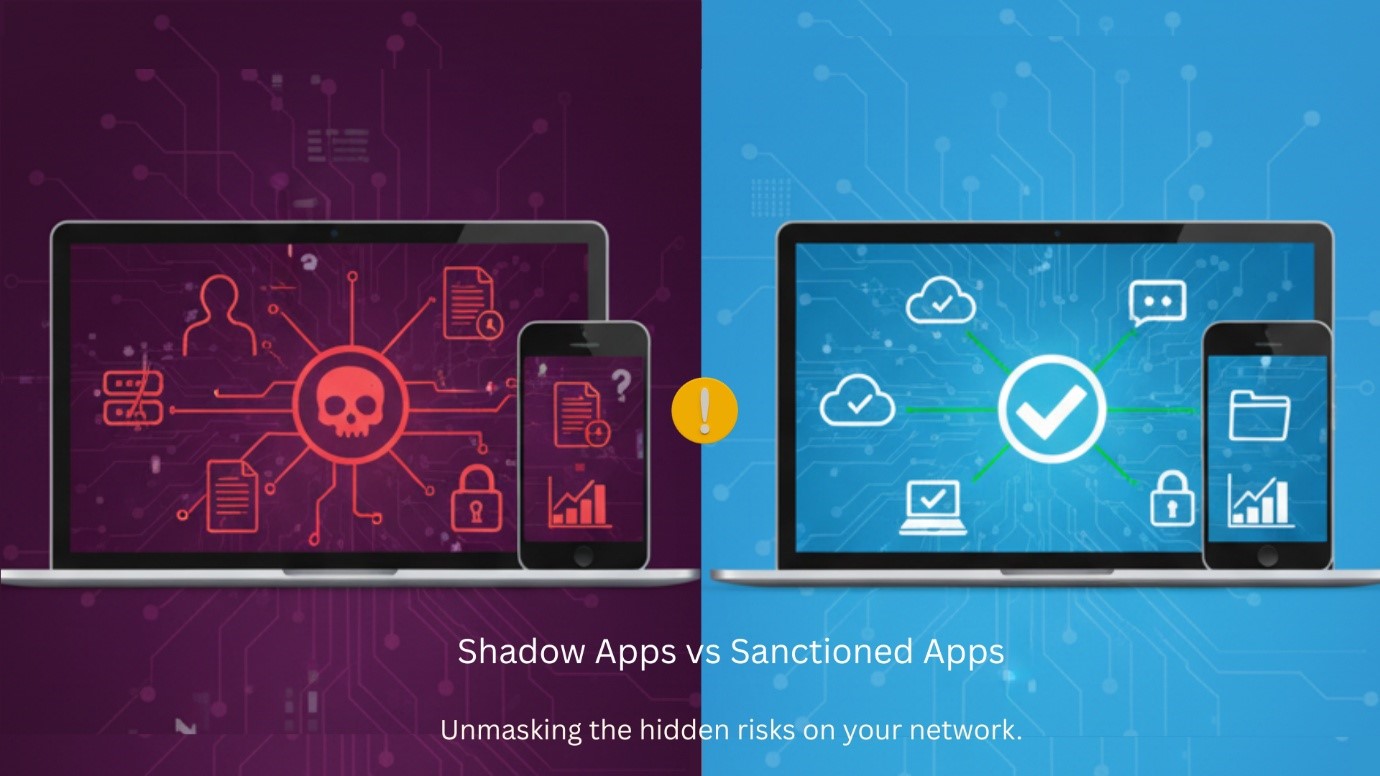
Shadow Apps vs. Sanctioned Apps: What Your Endpoint Data Is Telling You
Shadow Apps vs. Sanctioned Apps: What Your Endpoint Data…
Oct 16, 2025
-
0 Comments
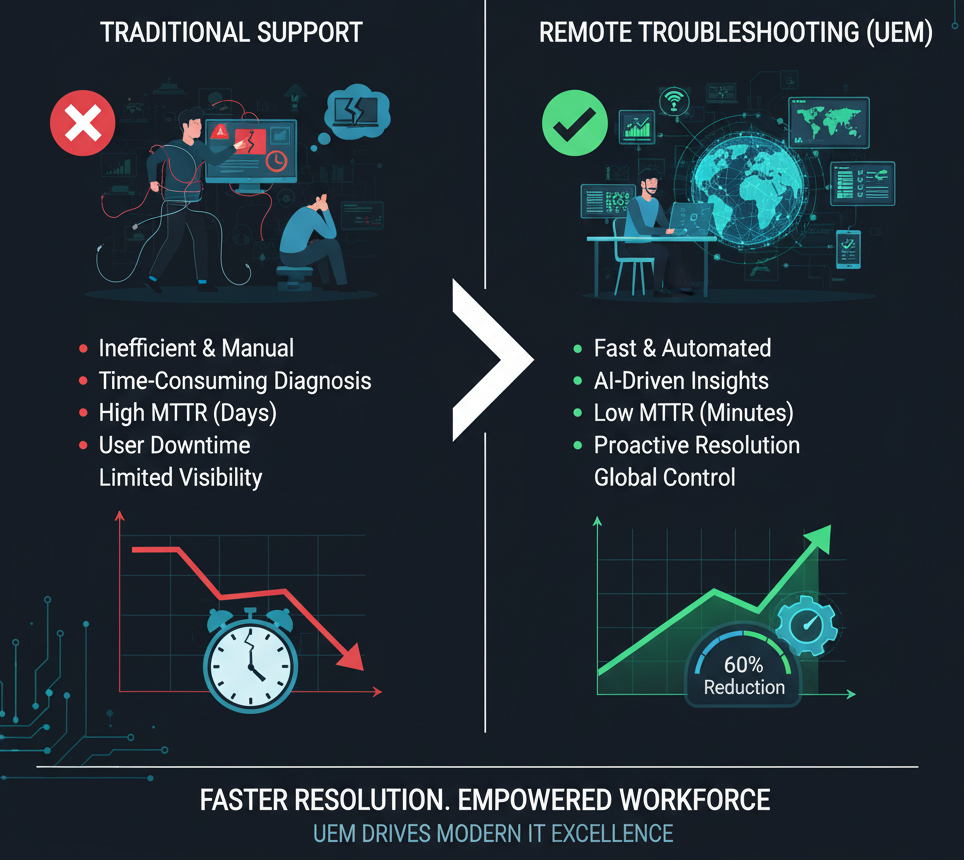
Remote Troubleshooting for the Win: Cut Down MTTR with UEM Insights
Remote Troubleshooting for the Win: Cut Down MTTR with…

Oct 16, 2025
-
0 Comments
Predictive Maintenance with Asset Intelligence: Stay One Step Ahead of Device Failures
BYOD Best Practices: Secure employee devices without killing productivity…

Oct 16, 2025
-
0 Comments
Is Your Organization Ready for BYOD? A 10-Point Compliance Checklist
Is Your Organization Ready for BYOD? A 10-Point Compliance…
Oct 16, 2025
-
0 Comments
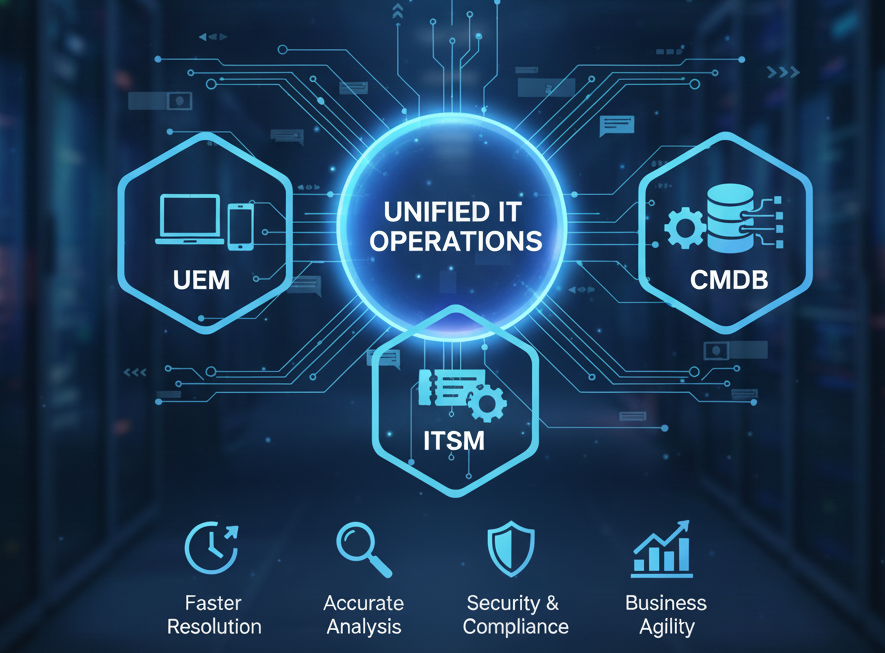
Integrating UEM with ITSM & CMDB: A Blueprint for Unified IT Operations
Integrating UEM with ITSM & CMDB: A Blueprint for…
Oct 16, 2025
-
0 Comments
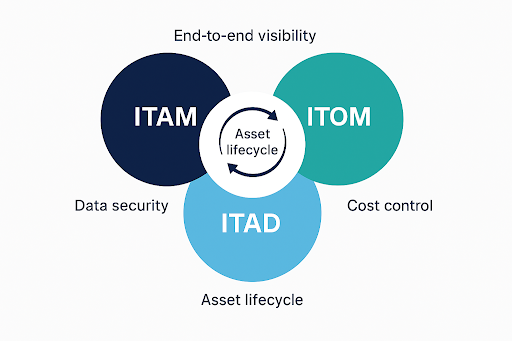
From Chaos to Control : How ITAM, ITOM and ITAD align to secure your enterprise
From Chaos to Control : How ITAM, ITOM and…

Sep 04, 2025
-
0 Comments
BYOD Best Practices: Secure employee devices without killing productivity
BYOD Best Practices: Secure employee devices without killing productivity…